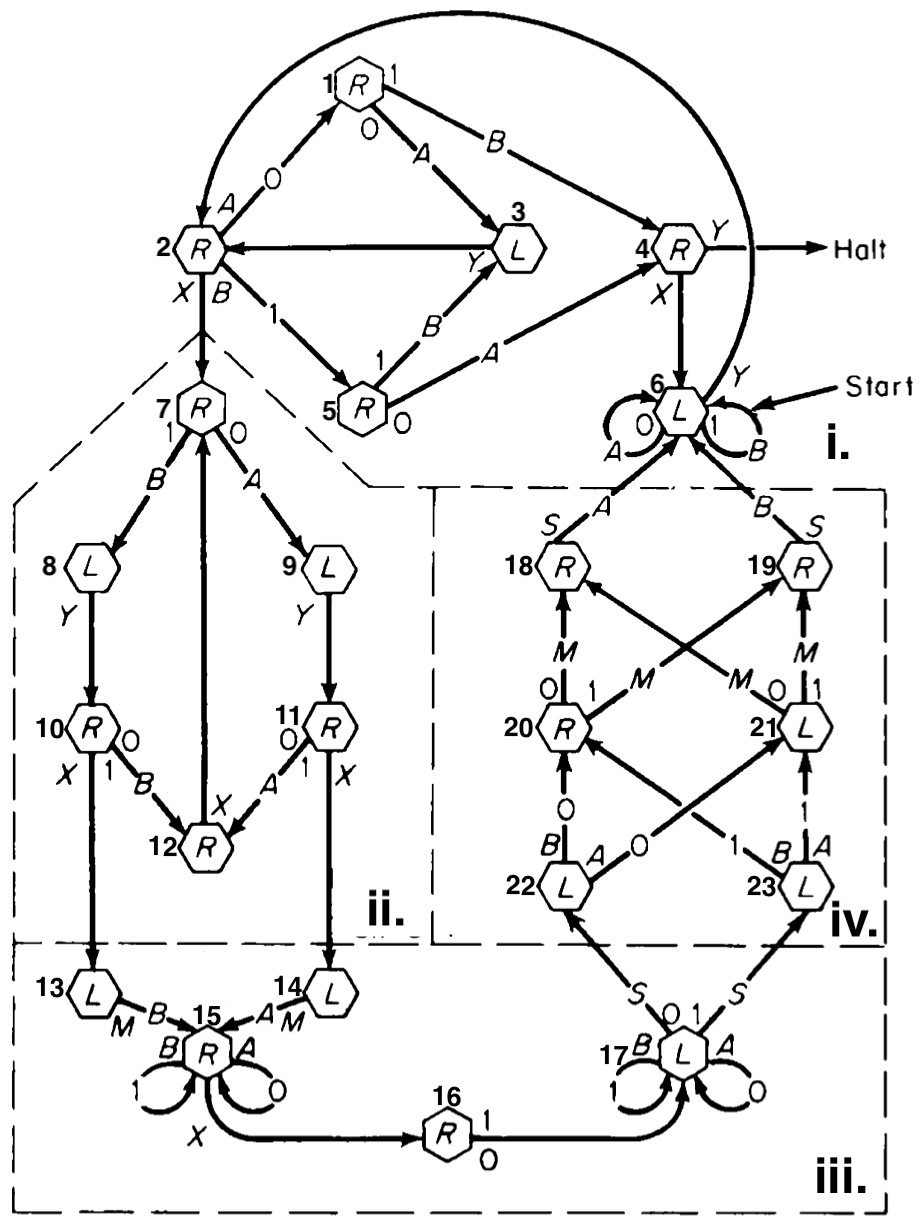
Phases i: Locating current quintuple ii: Copying next quintuple id and remembering symbol to write iii: Writing the symbol and housekeeping iv: Move head
0000M000000Y001X0000001X0010110X0100011X0110100Y00
For details, see the paper Johnson, Pontus, Intrinsic Propensity for Vulnerability in Computers? Arbitrary Code Execution in the Universal Turing Machine, 2021. and the Python implementation.